Breach & Attack Simulation, Vulnerability Assessment and Penetration Testing in Cyber Risk Management

Companies and organizations are constantly looking for techniques, tactics and procedures to better protect their data and assets from cyber risk.
The pervasive use of the Web and new modes of collaboration have dramatically accelerated this trend, making it increasingly complex and expensive to keep up.
Among the tools that can be used to protect against cyber dangers, efficient Risk Analysis and Cyber Risk Management helps considerably. Techniques used in these kind of activities include Breach & Attack Simulation, Vulnerability Assessment and Penetration Testing.
Let’s learn more about Cyber Risk Management and its distinctive techniques and traits.
Risk Analysis and Cyber Risk Management
Risk Analysis, and more generally Cyber Risk Management are processes for assessing the risks associated with the use of an information system or technology, aimed at supporting companies in developing risk management plans to mitigate/eliminate related threats.
The objective of Cyber Risk Management and Risk Analysis is to identify potential risks associated with the use of an information system and to assess the impact these might have on the company or organization.
Essentially, it involves a series of risk assessment techniques, such as assessment matrices, to identify potential risks associated with the use of a technology based on the probability of occurrence and the impact these could have on the company or organization.
In addition to these activities, we can also make use of proactive tactics, such as Vulnerability Assessments, Penetration Tests, or Breach & Attack Simulation.
What is a Vulnerability Assessment?
A Vulnerability Assessment is a technique used to identify vulnerabilities in computer systems and assess the risk of a possible attack by hackers or other malicious actors.

It consists of the systematic analysis of applications, systems, and networks to identify any vulnerabilities that could be used by hackers or other malicious parties to gain access to or compromise a system.
The Vulnerability Assessment process uses a variety of techniques and tools, including port scanning, web application vulnerability testing, and mobile device scanning, in order to identify possible vulnerabilities.
Vulnerability Assessment is a key cybersecurity activity, as it enables the identification of vulnerabilities in systems and assesses the risk of attacks by hackers or other threat actors.
It also enables organizations to take a proactive approach to cybersecurity, preventing attacks before they occur.
What is a Penetration Test?
![]() Penetration tests consist of a simulation of cyber attacks against an organization’s systems in order to identify and assess vulnerabilities.
Penetration tests consist of a simulation of cyber attacks against an organization’s systems in order to identify and assess vulnerabilities.
A penetration test – also called “pen test” or “ethical hacking” – is a simulation of a cyber attack by a team of cybersecurity experts to identify and assess vulnerabilities in an organization’s systems.
Penetration tests can be performed on any type of computer system, including web applications, networks, servers, mobile devices, desktop computers and other devices.
They are often conducted by cybersecurity experts outside the organization, known as “penetration testers” or “ethical hackers,” who use the same tools and techniques used by malicious hackers.
What is a Breach & Attack Simulation?
A Breach & Attack Simulation (BAS) is a security test that simulates a cyber attack from the hacker’s perspective.
Instead of trying to break into the system using hacking techniques, the team of cybersecurity experts simulates a cyber attack using tools and techniques that real hackers commonly use.
Breach & Attack Simulation then simulates a cyber attack in a comprehensive and realistic way, assessing the security of the system similarly to what a hacker would do.
This includes assessing the security of web applications, servers, networks, mobile devices, and cloud infrastructure.
The goal of Breach & Attack Simulation is to identify system weaknesses and provide recommendations for improving security.
Differences between Penetration Test and Breach & Attack Simulation
Penetration Test and Breach & Attack Simulation have similar objectives, but differ in their methodology of execution.
Penetration testing uses real hacking techniques to try to penetrate the system, while Breach & Attack Simulation uses tools and techniques similar to those used by real hackers to simulate a cyber attack.
In addition, the Penetration Test is more in-depth and considers all possible vulnerabilities in the system, while the Breach & Attack Simulation focuses on a specific attack and simulates only the techniques used in that attack.
Both Penetration Test and Breach & Attack Simulation are useful in identifying system weaknesses and providing recommendations for improving security.
However, Breach & Attack Simulation is more useful when you want to simulate a specific attack or when you want to test the organization’s ability to respond in the event of a cyber attack.
On the other hand, Penetration Testing is more useful when you want to identify all possible vulnerabilities in the system and when you want to test the security of the system in depth.
Telsy’s Cyber Risk Management
To face the complications and risks derived from malicious actors or software vulnerabilities, Telsy offers a coaching and support service to companies aimed at assessing the degree of risk exposure of information and technology assets and implementing sustainable and effective remediation plans.
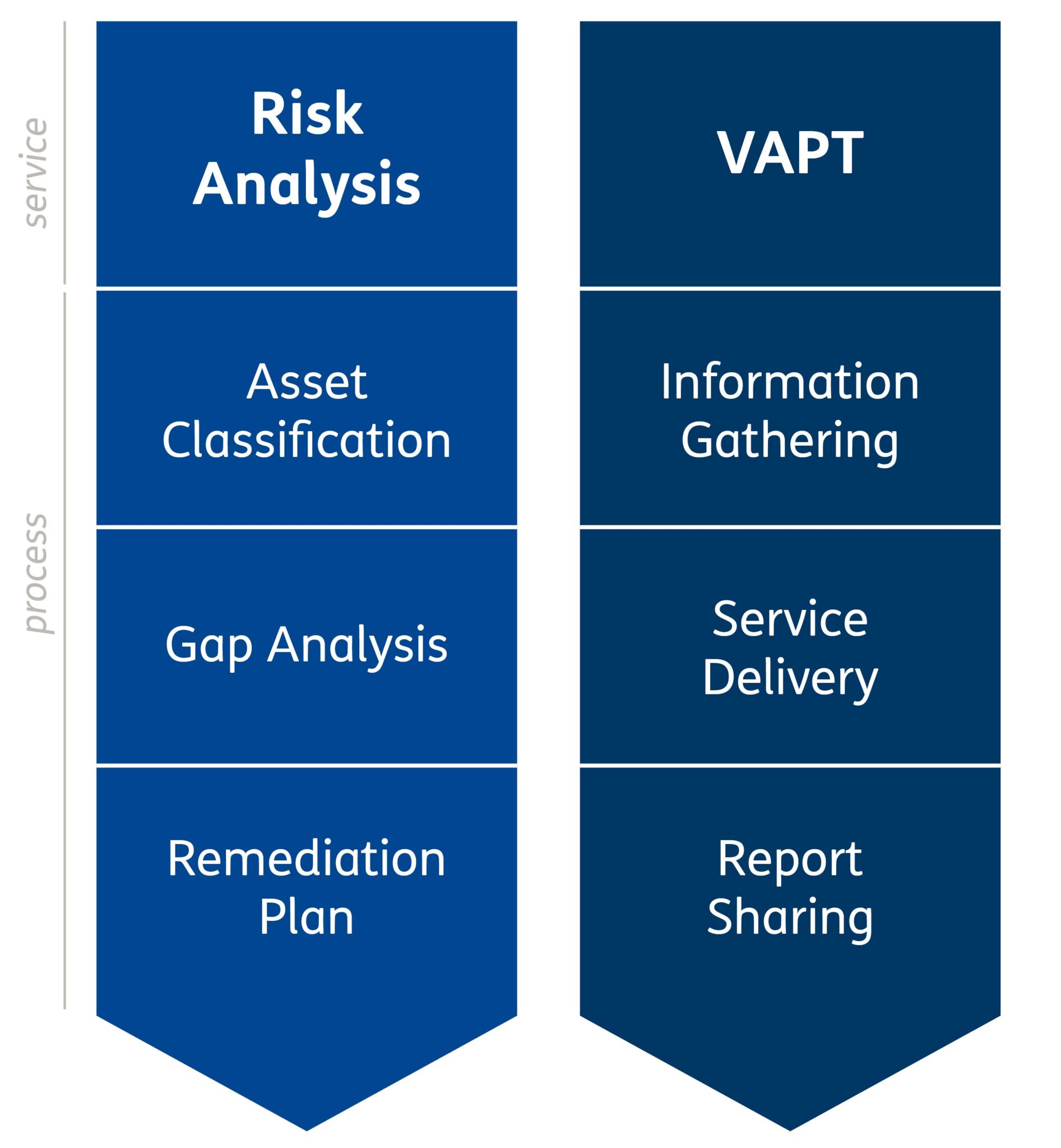 The service includes two macro areas:
The service includes two macro areas:
Risk Analysis
The Risk Analysis process is based on the adoption of industry standards and best practices and enables the definition, implementation and maintenance of a risk management model integrated into business processes, ensuring the homogeneity, consistency and repeatability of the achieved results.
Vulnerability Assessment / Penetration Test (VAPT)
VAPT activities, carried out following industry best practices, are performed through mixed techniques, combining the use of automatic tools with manual activities in order to verify the security status of systems, detect any vulnerabilities and their subsequent exploitation. These activities include Vulnerability Assessment, Penetration Testing and Breach & Attack Simulation techniques.
Learn more about Telsy’s solutions for Cyber Risk Management services and other preventive and reactive security tools dedicated to businesses.
